Decoding Crypto: Understanding the Code Behind Blockchain Technology
Estimated reading time: 11 minutes
Key Takeaways
- The “crypto code” is the underlying foundation that makes cryptocurrencies and blockchains both secure and decentralized.
- Top crypto programming languages include Java, Python, Solidity, Rust, and Vyper—each serving different purposes in Web3 development.
- Architectural features like block structure, validation logic, and consensus mechanisms secure assets without the need for a central authority.
- Smart contracts enable programmable, automated financial applications and NFTs, shaping the future of digital economies.
- New career opportunities are opening for developers, engineers, and cryptography experts as blockchain adoption accelerates worldwide.
Table of Contents
Introduction
While many crypto enthusiasts focus on price charts and trading strategies, the true magic of cryptocurrency happens beneath the surface—in the lines of code that make blockchain technology possible. The crypto code is the invisible architecture that powers everything from Bitcoin transactions to complex DeFi protocols (blockchain basics).

But what exactly is this code? How does it work? And why should you care if you’re not a developer?
In this comprehensive guide, we’ll peel back the digital curtain and explore the programming languages, cryptographic principles, and security mechanisms that make up the backbone of the entire crypto ecosystem. Whether you’re a trader looking to understand what you’re investing in, a potential developer exploring new career paths, or simply curious about how blockchain really works, this post will give you the knowledge foundation you need (introduction to crypto).
What Is Crypto Code? The Digital DNA of Blockchain
Crypto code is the comprehensive set of programming and cryptographic elements that power cryptocurrencies and blockchain systems. This isn’t just any type of software—it’s specialized code designed to create secure, transparent, and decentralized digital systems that can operate without central authorities.
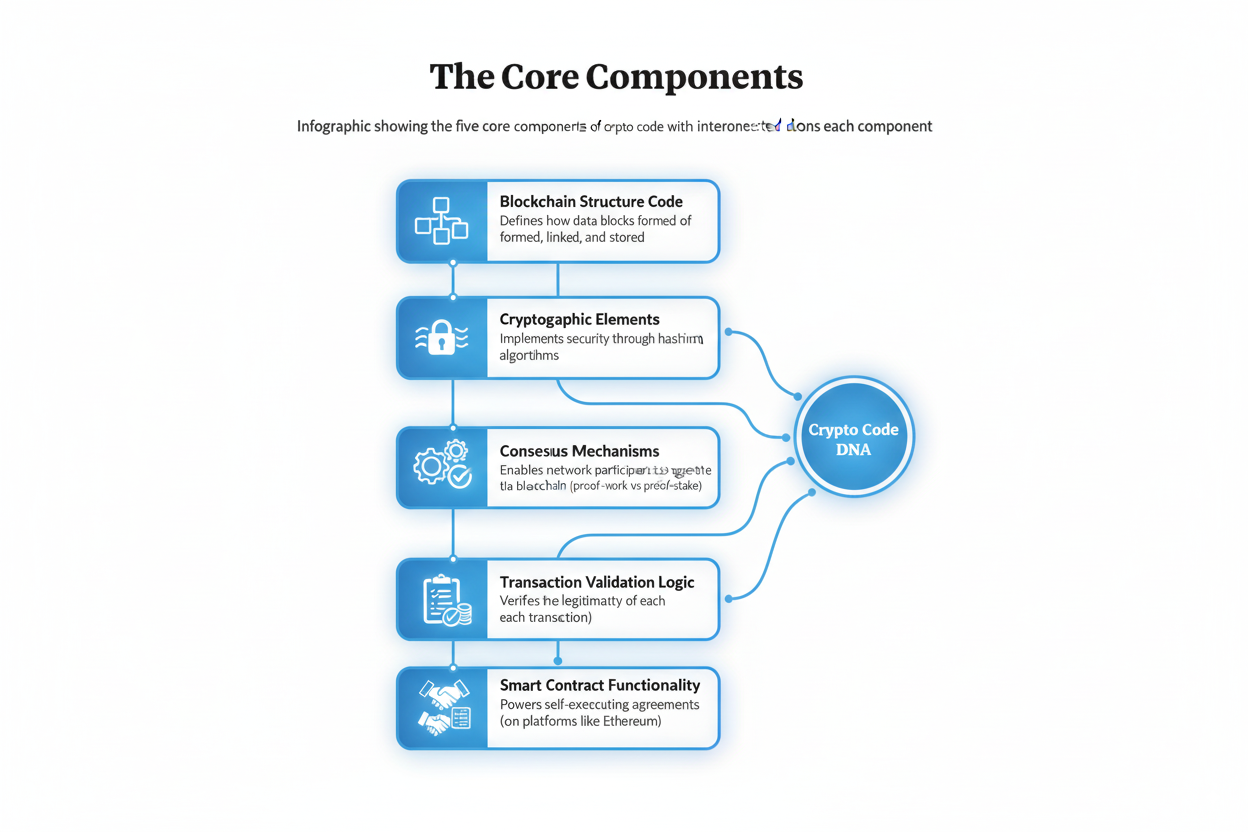
The Core Components
- Blockchain Structure Code: Defines how data blocks are formed, linked, and stored
- Cryptographic Elements: Implements security through hashing and encryption algorithms
- Consensus Mechanisms: Enables network participants to agree on the valid state of the blockchain (proof-of-work vs proof-of-stake)
- Transaction Validation Logic: Verifies the legitimacy of each transaction
- Smart Contract Functionality: Powers self-executing agreements (on platforms like Ethereum)
Q: How is crypto code different from traditional programming?
A: Unlike conventional software that typically runs on centralized servers, crypto code operates across distributed networks of computers (nodes). It must be designed to:
- Function without a central authority
- Maintain security in a trustless environment
- Achieve consensus among network participants
- Ensure immutability of recorded data
- Process transactions transparently yet securely (how cryptocurrency works)
For instance, when you send Bitcoin to someone, the code handles validating your ownership, verifying you haven’t already spent those coins, creating a cryptographic record of the transaction, and adding it to the blockchain—all without requiring a bank or payment processor to oversee the process (history of Bitcoin).
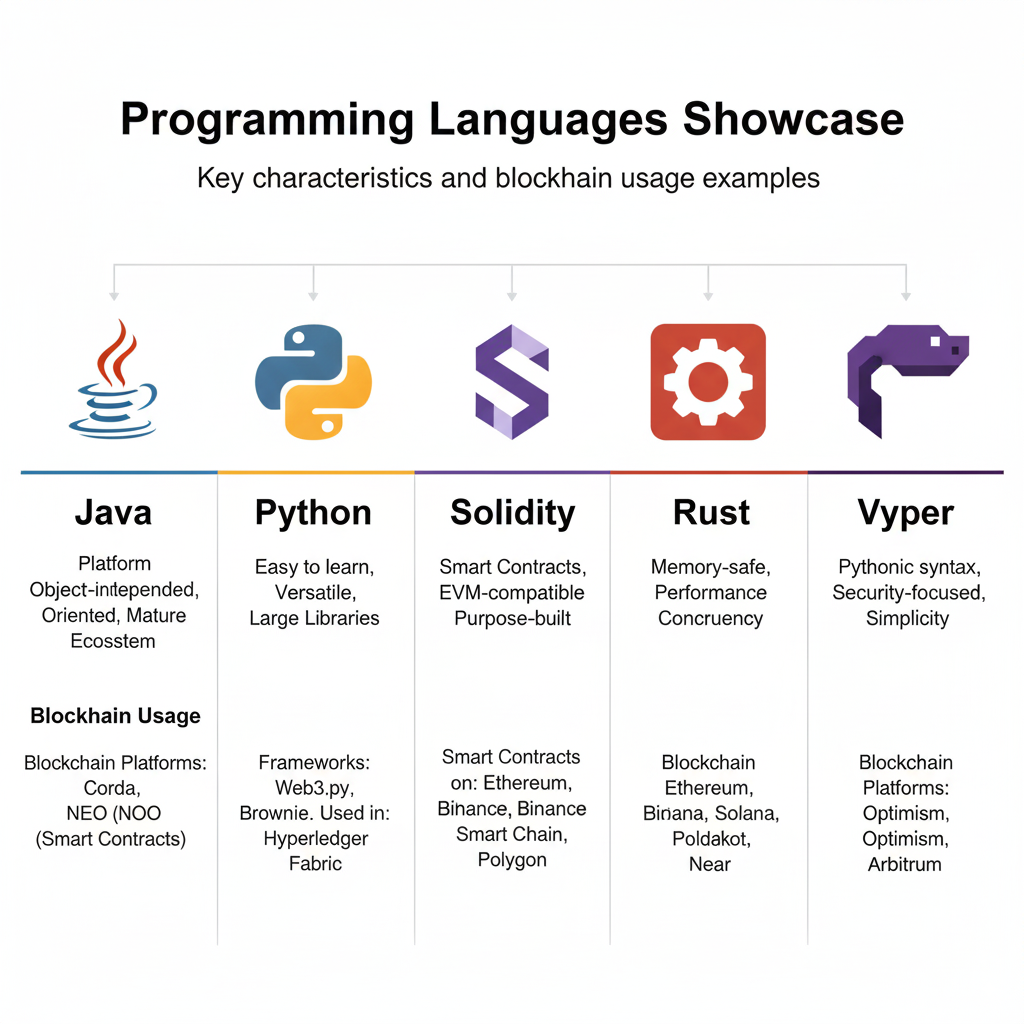
The Languages Behind the Crypto Revolution
Different blockchains and crypto projects utilize various programming languages, each with unique strengths and applications:
Java: The Enterprise-Grade Blockchain Builder
Strengths: Portability, scalability, and extensive libraries
Used in: Hyperledger Fabric, NEO, IOTA
Java’s “write once, run anywhere” capability makes it ideal for enterprise blockchain development. Its mature ecosystem and strong typing help create robust, scalable blockchain infrastructure.
// Example: Simple block structure in Java
public class Block {
private String hash;
private String previousHash;
private String data;
private long timeStamp;
public Block(String data, String previousHash) {
this.data = data;
this.previousHash = previousHash;
this.timeStamp = System.currentTimeMillis();
this.hash = calculateHash();
}
public String calculateHash() {
// Hash calculation implementation
}
}
Python: The Blockchain Prototyper
Strengths: Readability, rapid development, excellent for prototyping
Used in: NEO, Steem, Hyperledger Fabric (parts)
Python’s simplicity and extensive libraries make it perfect for quickly developing and testing blockchain concepts. While not always used in production environments, it’s invaluable for proof-of-concept work.
# Example: Simple blockchain in Python
import hashlib
import time
class Block:
def __init__(self, index, previous_hash, timestamp, data, hash):
self.index = index;
self.previous_hash = previous_hash;
self.timestamp = timestamp;
self.data = data;
self.hash = hash;
def calculate_hash(index, previous_hash, timestamp, data):
value = str(index) + str(previous_hash) + str(timestamp) + str(data);
return hashlib.sha256(value.encode('utf-8')).hexdigest()
Solidity: The Smart Contract Specialist
Strengths: Purpose-built for smart contracts, Ethereum compatibility
Used in: Ethereum (what are smart contracts), Binance Smart Chain, Polygon, and other EVM-compatible chains
Solidity is the dominant language for creating smart contracts—self-executing agreements with the terms written directly into code.
// Example: Simple smart contract in Solidity
pragma solidity ^0.8.0;
contract SimpleStorage {
uint private storedData;
function set(uint x) public {
storedData = x;
}
function get() public view returns (uint) {
return storedData;
}
}
Rust: The Security-Focused Performer
Strengths: Memory safety, performance, concurrency
Used in: Solana, Polkadot, Near Protocol
Rust has gained significant traction for building high-performance blockchains due to its focus on memory safety without sacrificing speed.
// Example: Simple blockchain structure in Rust
struct Block {
index: u64,
timestamp: u64,
previous_hash: String,
hash: String,
data: String,
}
impl Block {
fn calculate_hash(&self) -> String {
// Hash calculation implementation
}
}
Vyper: The Safety-First Alternative
Strengths: Security, simplicity, auditability
Used in: Ethereum (alternative to Solidity)
Vyper was designed as a more secure alternative to Solidity, eliminating features that could lead to vulnerabilities.
# Example: Simple contract in Vyper
stored_data: uint256
@external
def set(x: uint256):
self.stored_data = x
@external
@view
def get() -> uint256:
return self.stored_data
Blockchain Architecture & Security: How Crypto Code Keeps Your Assets Safe
Understanding how blockchain architecture works helps explain why cryptocurrencies can operate securely without central oversight. Let’s break down the key components (distributed ledger technology):
Block Structure: The Foundation of Immutability
- Block Header: Contains metadata like timestamp, nonce, and Merkle root
- Previous Block Hash: Links to the previous block, creating the “chain”
- Transaction Data: The actual information being stored
- Current Block Hash: A unique identifier created by hashing the block’s contents
This structure makes blockchain data immutable—changing any information in a block would alter its hash, breaking the chain and making the manipulation evident to all network participants.
Transaction Validation: Ensuring Legitimacy
Before a transaction joins the blockchain, crypto code verifies:
- Ownership: The sender has the private keys corresponding to the funds
- Sufficient Balance: The sender has enough cryptocurrency to complete the transaction
- Proper Formatting: The transaction follows the protocol’s rules
- No Double Spending: The same cryptocurrency hasn’t already been sent elsewhere
For example, in Bitcoin, nodes run validation code that checks digital signatures against public keys to verify ownership before accepting transactions into the mempool for mining (mining explained).
Consensus Mechanisms: Agreeing Without Authority
Different blockchains use various consensus algorithms to agree on the valid state of the network:
Proof of Work (PoW)
- Used by: Bitcoin, Litecoin, Dogecoin
- How it works: Miners compete to solve complex mathematical puzzles, with the winner getting to add the next block
- Security comes from: The massive computational power needed to control the network
Proof of Stake (PoS)
- Used by: Ethereum 2.0, Cardano, Solana
- How it works: Validators are selected to create blocks based on how much cryptocurrency they’ve “staked” as collateral
- Security comes from: Financial incentives to maintain network integrity
Delegated Proof of Stake (DPoS)
- Used by: EOS, Tron
- How it works: Token holders vote for a limited number of validators who take turns producing blocks
- Security comes from: Reputation and continued community support
For an in-depth comparison of these mechanisms, see:
proof-of-work vs proof-of-stake
Cryptographic Security Elements
Crypto code relies heavily on several cryptographic techniques:
Hashing Functions
- Convert data of any size into fixed-length strings
- Create unique, deterministic outputs for any input
- Make it virtually impossible to reverse-engineer the original data
- Example: Bitcoin uses SHA-256 to create block hashes
Public-Private Key Cryptography
- Creates mathematically linked key pairs
- Private key: Kept secret, used to sign transactions
- Public key: Shared openly, used to verify signatures
- Creates digital signatures that prove ownership without revealing private keys
Smart Contracts & DApps: Programming Money
Smart contracts represent one of the most revolutionary applications of crypto code—they’re self-executing contracts with the terms directly written into code (what are smart contracts).
How Smart Contracts Work
When certain conditions are met, smart contracts automatically execute predefined actions. For example, a smart contract might:
- Hold funds in escrow until delivery confirmation
- Automatically distribute royalties when digital content is purchased
- Execute complex DeFi operations like providing liquidity or issuing loans
Real-World Applications
Decentralized Finance (DeFi)
// Simplified DeFi lending contract
pragma solidity ^0.8.0;
contract SimpleLending {
mapping(address => uint) public deposits;
mapping(address => uint) public loans;
function deposit() public payable {
deposits[msg.sender] += msg.value;
}
function borrow(uint amount) public {
require(amount <= deposits[msg.sender] * 2, "Insufficient collateral"); loans[msg.sender] += amount; payable(msg.sender).transfer(amount); } function repay() public payable { require(loans[msg.sender] > 0, "No outstanding loans");
require(msg.value <= loans[msg.sender], "Repayment exceeds loan");
loans[msg.sender] -= msg.value;
}
}
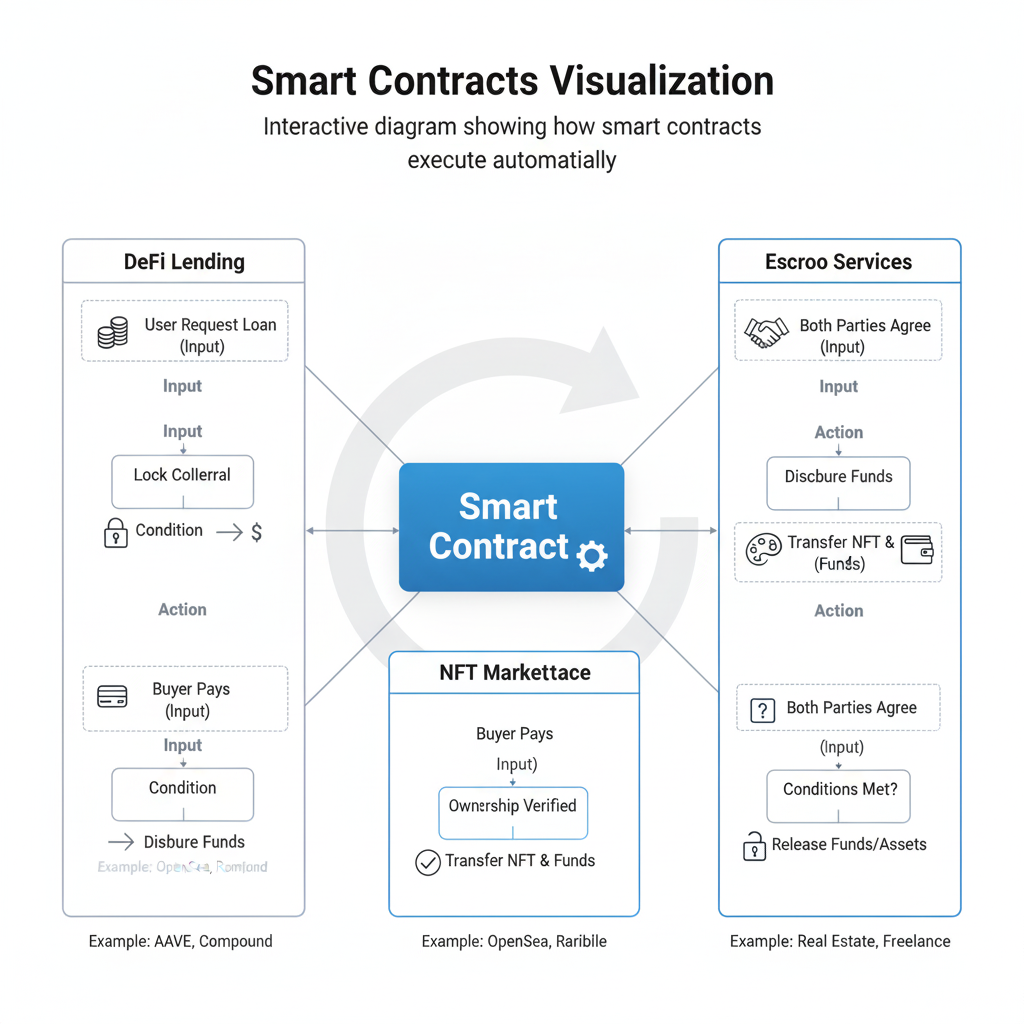
NFT Marketplaces
// Simplified NFT marketplace contract
pragma solidity ^0.8.0;
import "@openzeppelin/contracts/token/ERC721/IERC721.sol";
contract SimpleNFTMarketplace {
struct Listing {
address seller;
uint price;
bool active;
}
mapping(address => mapping(uint => Listing)) public listings;
function listNFT(address nftContract, uint tokenId, uint price) public {
IERC721(nftContract).transferFrom(msg.sender, address(this), tokenId);
listings[nftContract][tokenId] = Listing(msg.sender, price, true);
}
function buyNFT(address nftContract, uint tokenId) public payable {
Listing memory listing = listings[nftContract][tokenId];
require(listing.active, "NFT not for sale");
require(msg.value >= listing.price, "Insufficient payment");
listings[nftContract][tokenId].active = false;
IERC721(nftContract).transferFrom(address(this), msg.sender, tokenId);
payable(listing.seller).transfer(msg.value);
}
}
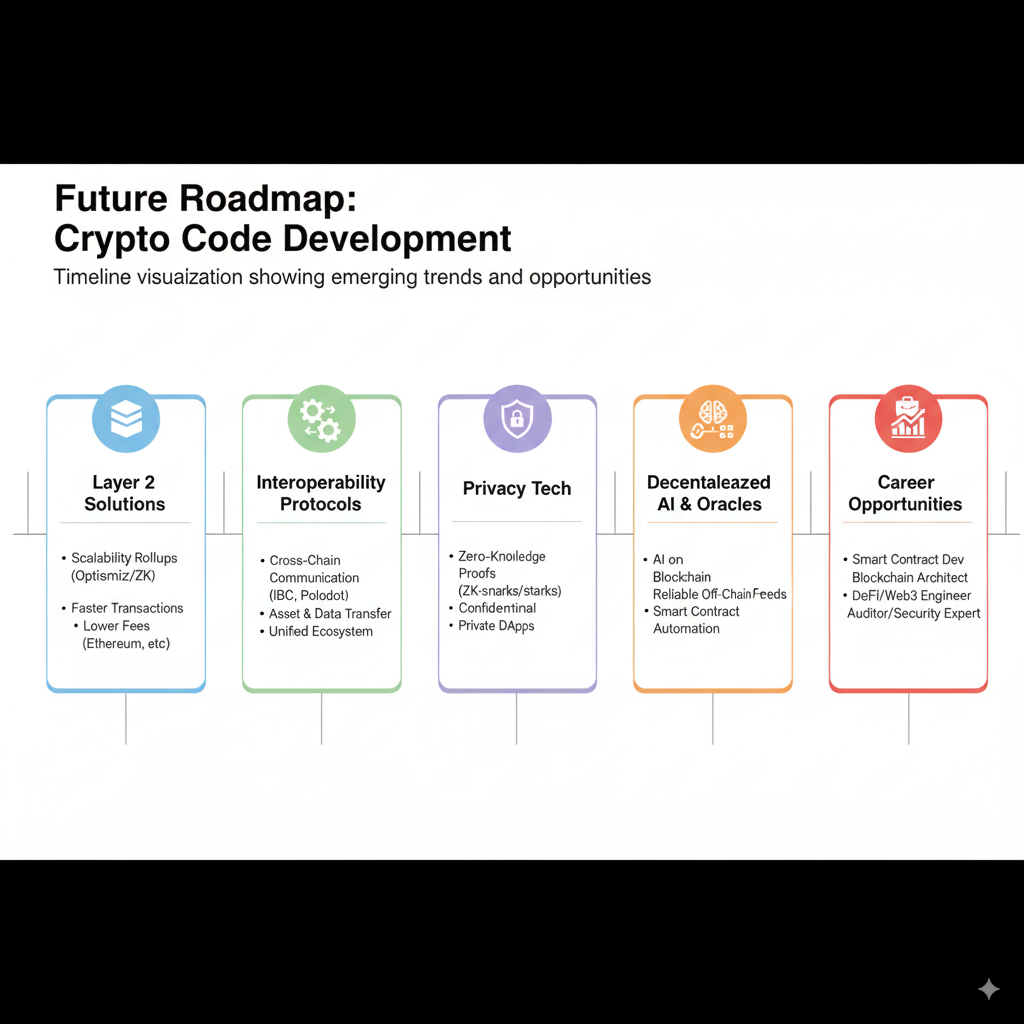
The Future of Crypto Code: What’s Next?
The world of crypto code is constantly evolving, with several exciting trends on the horizon:
Emerging Trends
- Layer 2 Scaling Solutions: Code frameworks like Optimistic Rollups and ZK-Rollups are addressing blockchain scalability
- Interoperability Protocols: Cross-chain communication frameworks allowing different blockchains to interact
- Privacy-Preserving Technologies: Zero-knowledge proofs and other cryptographic techniques enabling privacy while maintaining security
- Sustainable Consensus Mechanisms: Energy-efficient alternatives to traditional Proof of Work
Career Opportunities in Crypto Coding
The demand for blockchain developers continues to grow, with specialized roles including:
- Blockchain Core Developers
- Smart Contract Engineers (what are smart contracts)
- Security Auditors
- DApp Frontend Developers
- Cryptography Specialists
Getting Started with Crypto Coding
- Master the fundamentals: Learn JavaScript, Python, or another foundational language
- Understand blockchain basics: Study how Bitcoin and Ethereum work at a technical level (blockchain basics)
- Learn Solidity: For Ethereum and EVM-compatible chains
- Explore development frameworks: Truffle, Hardhat, Brownie, and Web3.js
- Practice with projects: Build simple DApps and smart contracts
- Join the community: Participate in hackathons and open source projects
Conclusion
The crypto code that powers blockchain technology represents one of the most significant innovations in computer science and finance of the 21st century. By combining cryptography, distributed systems, and economic incentives, these systems have created new possibilities for how we transfer value, establish trust, and build applications.
Whether you’re looking to invest in cryptocurrencies, develop blockchain applications, or simply understand this revolutionary technology, having a solid grasp of how crypto code works gives you a significant advantage. To dive deeper into the essentials and the entire ecosystem, visit our pillar guide: crypto trading for beginners.
At Affmiss, we’re committed to helping you navigate the complex world of cryptocurrency and blockchain technology. Stay tuned for more in-depth guides on trading strategies, affiliate programs, and emerging trends in the crypto space.
What aspect of crypto code interests you most? Share your thoughts in the comments below!
FAQ
What is crypto code and why does it matter?
Which programming languages should I learn for blockchain development?
How does cryptography secure blockchain transactions?
Are blockchains really unhackable?
How can I start building my own smart contract or DApp?
Where can I learn more about fundamental blockchain concepts?
